Log In With a Security Key
Since the beginning, Pro Custodibus has offered multi-factor authentication (MFA, aka two-factor authentication, 2FA, two-step verification, or secondary verification) via TOTP, which most people use via an “authenticator app” on their phone. We recently added a second MFA option: WebAuthn, which can be used via a physical “security key”, or a with a virtual security key managed by your browser or OS.
Although WebAuthn allows security keys to be used as a full replacement for usernames and passwords (often called “Passkeys” when used this way), Pro Custodibus only uses security keys for MFA, as a secondary factor. Using WebAuthn this way enables Pro Custodibus to also work with some older security keys that don’t have full Passkeys support, but do support U2F (Universal 2nd Factor).
In short, any device that advertises support for U2F, FIDO, or FIDO2 should be usable as an MFA “security key” with Pro Custodibus. Following is a quick guide to show you how to set it up and use it:
Add a Security Key
In the Pro Custodibus UI, navigate to your profile page by clicking your name in the header:
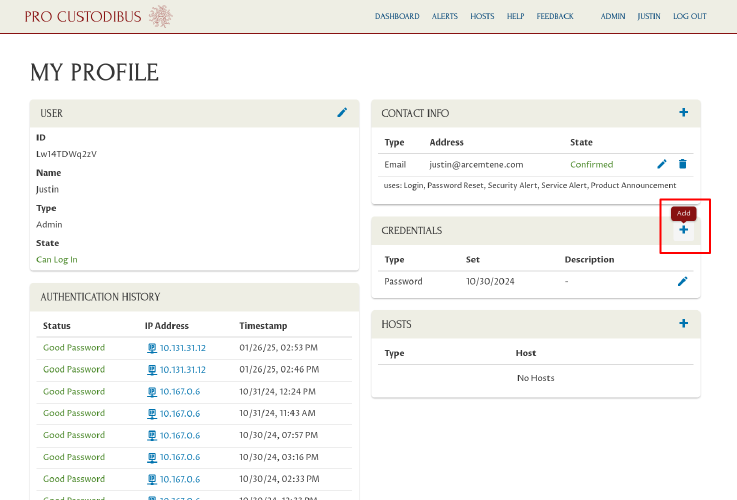
On your profile page, find the Credentials panel, and click its Add icon:
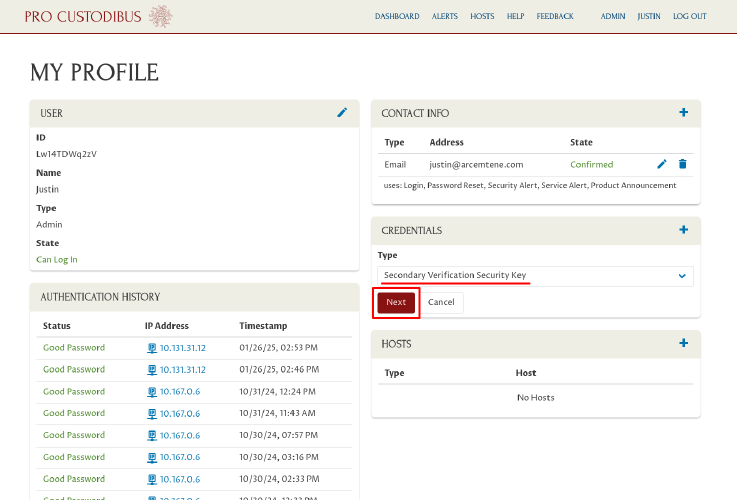
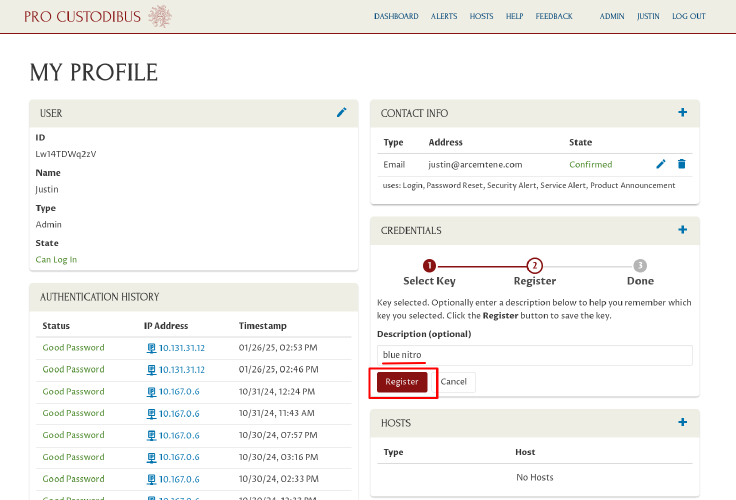
Select Secondary Verification Security Key from the Type dropdown, and click the Next button:
Then click the Select Key button:
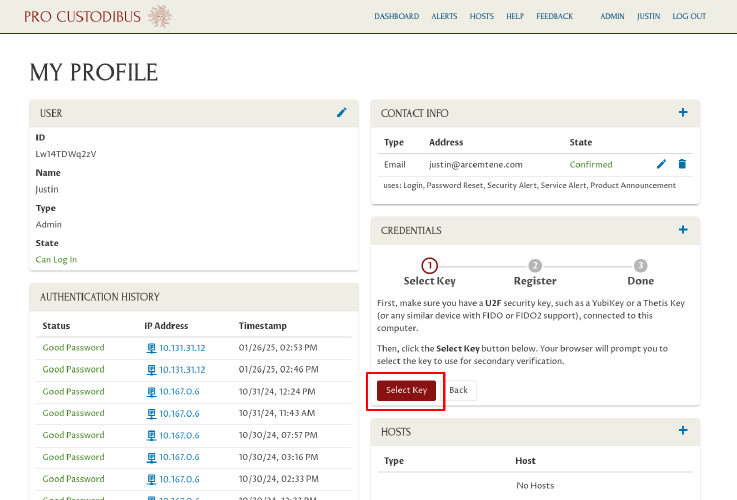
This will trigger your browser to prompt you with the available security key options on your computer. The UI for this varies greatly among browsers and operating systems; with Firefox on Linux, with one security key available, the prompt looks like this:
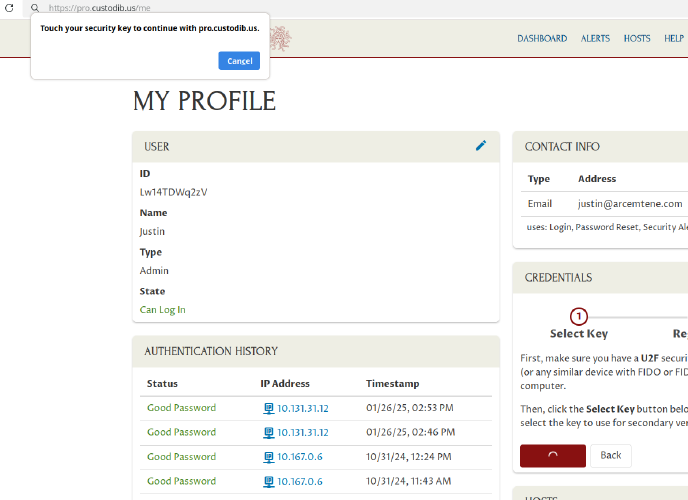
If you select a key (in this example, by touching the physical security key with your finger), you can then enter a description for the key in the Description field (to help you remember which of your security keys you’ve registered). To complete the process, click the Register button:
The UI will now show you a secret Recovery Code that you can use one time for secondary verification, in case you lose access to all the secondary-verification devices you’ve registered. Copy this recovery code to a safe place; then click the Done button:
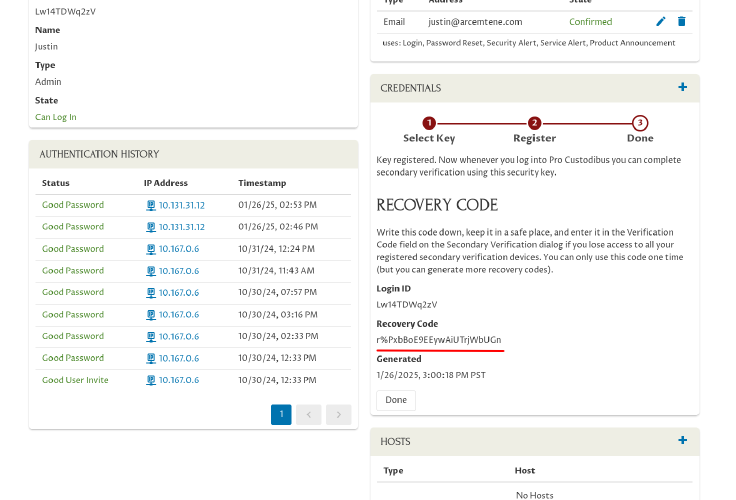
Now log out of Pro Custodibus, so you can try logging in with your security key.
Log In With a Security Key
Once you’ve registered a security key, on the Log In page of Pro Custodibus, enter your login ID and password as usual, and click the Log In button:
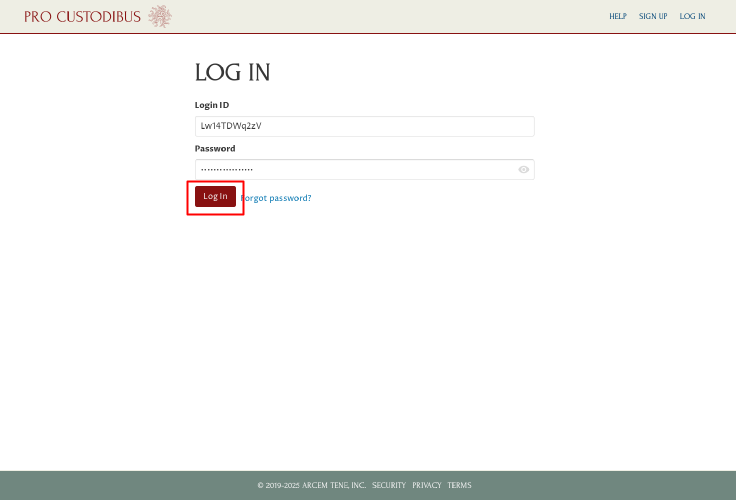
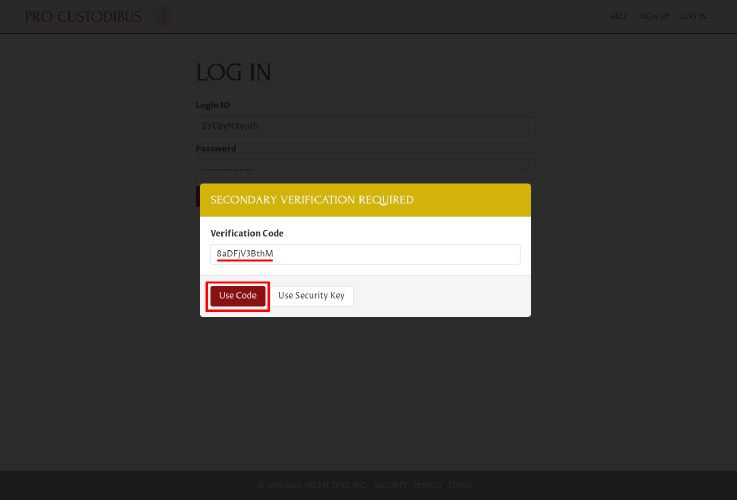
A Secondary Verification Required dialog will appear, asking you to either use a code, or a key. Click the Use Security Key button:
|
Tip
|
If you don’t have access to any of your security keys, you can enter a one-time recovery or bypass code, or a code from an authenticator app that you’ve registered with Pro Custodibus, into the Verification Code field (and then click the Use Code button). |
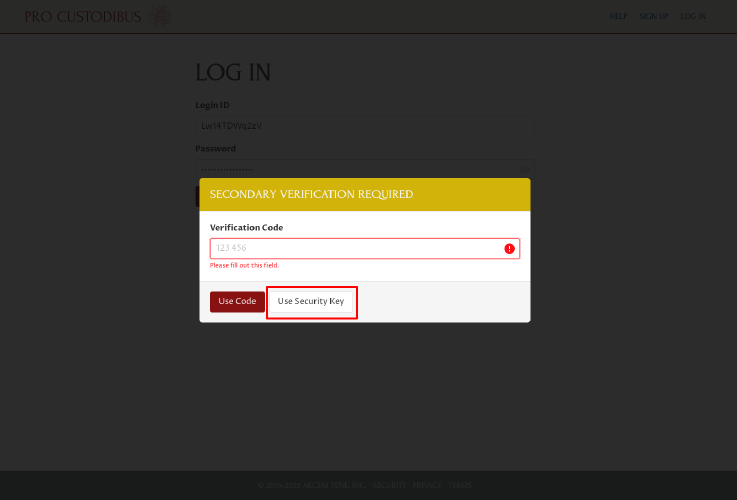
The Use Security Key button will trigger your browser to prompt you to use one of the available security key options on your computer. The UI for this varies greatly among browsers and operating systems; with Firefox on Linux, with one security key available, the prompt looks like this:
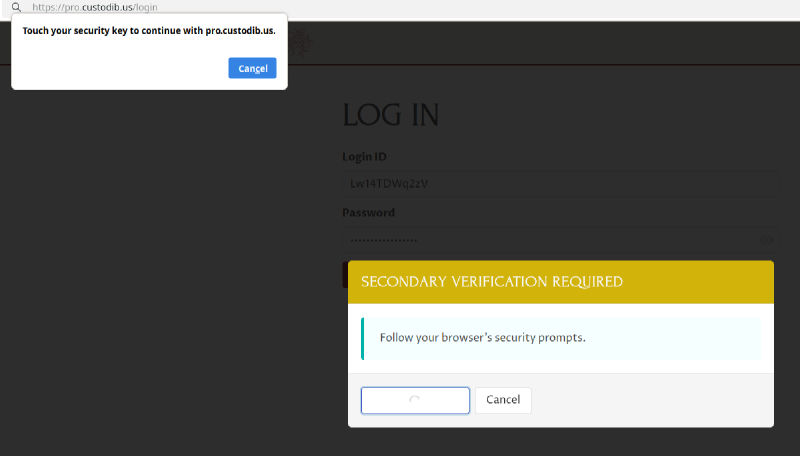
If you select a key that you’ve registered with Pro Custodibus (in this example, by touching the physical security key with your finger), this will complete the log-in process, and you will be logged into Pro Custodibus.
If you select a key that you have not registered with Pro Custodibus, you’ll see a generic error message like the following:
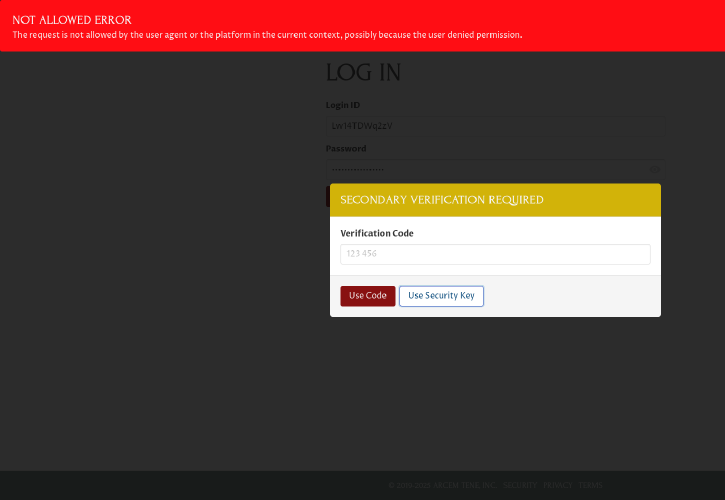
In that case, you can click the Use Security Key button again to try a different key.
Add Another Recovery Code
If you want to set up additional recovery codes, go back to your profile page, and click the Add icon in the Credentials panel again:
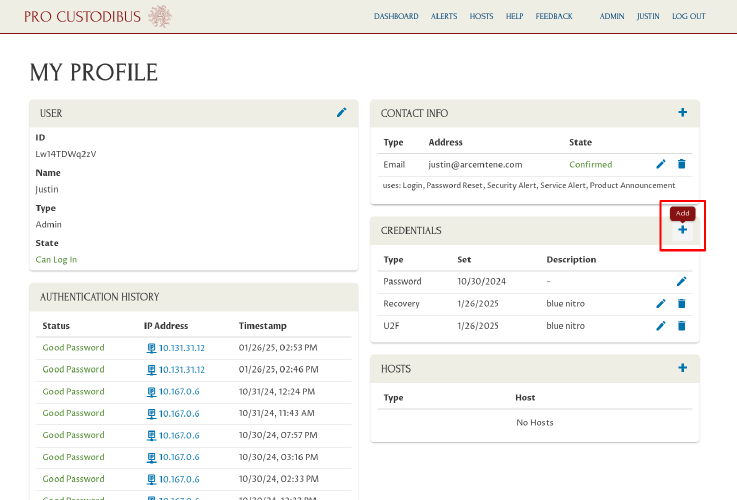
Select Secondary Verification Recovery Code from the Type dropdown, and click the Next button:
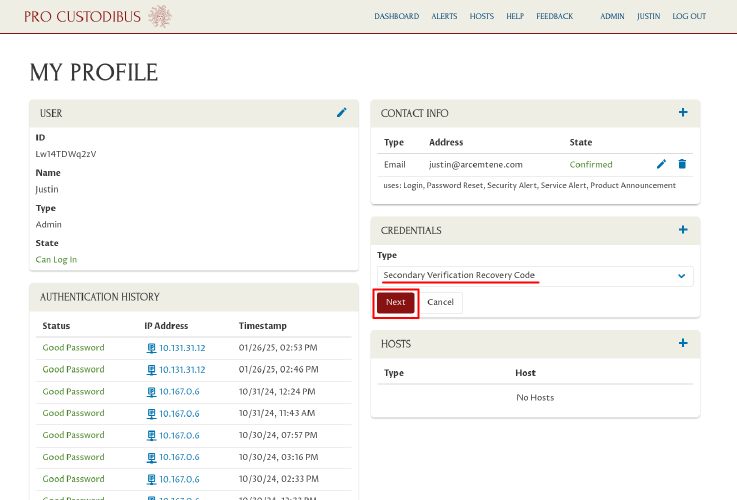
A Secondary Verification Required dialog will appear, asking you to either use a code, or a key. Click the Use Security Key button:
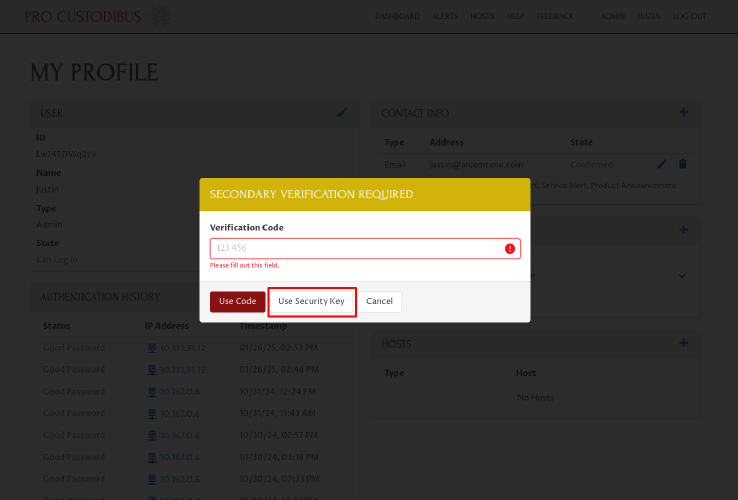
This will trigger your browser to prompt you to use one of the available security key options on your computer. The UI for this varies greatly among browsers and operating systems; with Firefox on Linux, with one security key available, the prompt looks like this:
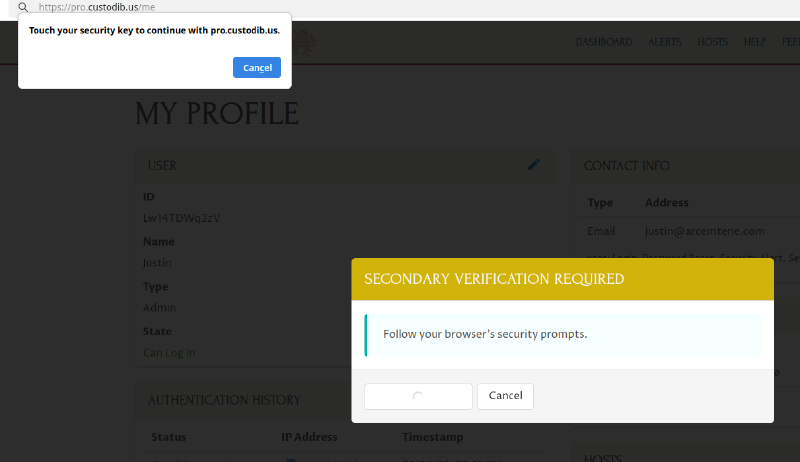
If you select a key that you’ve registered with Pro Custodibus (in this example, by touching the physical security key with your finger), you can then enter a description for the new recovery code in the Description field (to help you remember which recovery code it is, or where you’re going to store the code). To generate the code, click the Generate button:
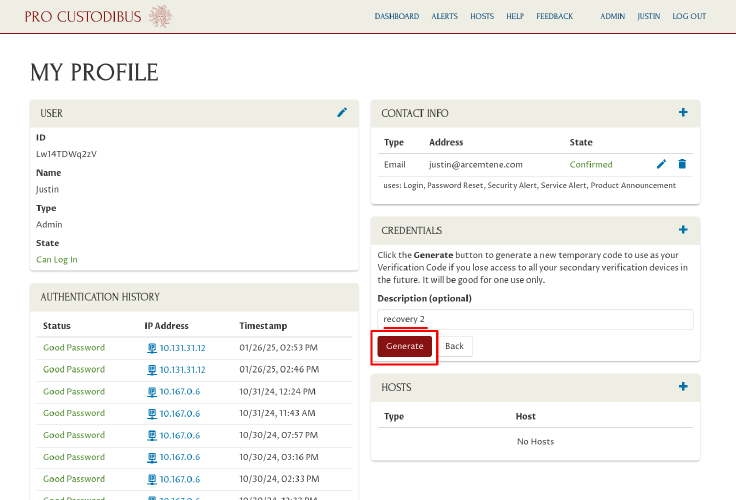
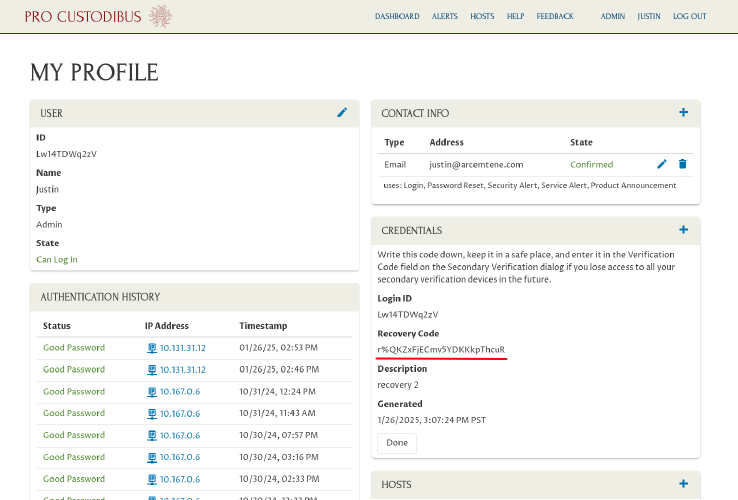
The UI will now show you a new secret Recovery Code that you can use one time for secondary verification. Copy this recovery code to a safe place; then click the Done button:
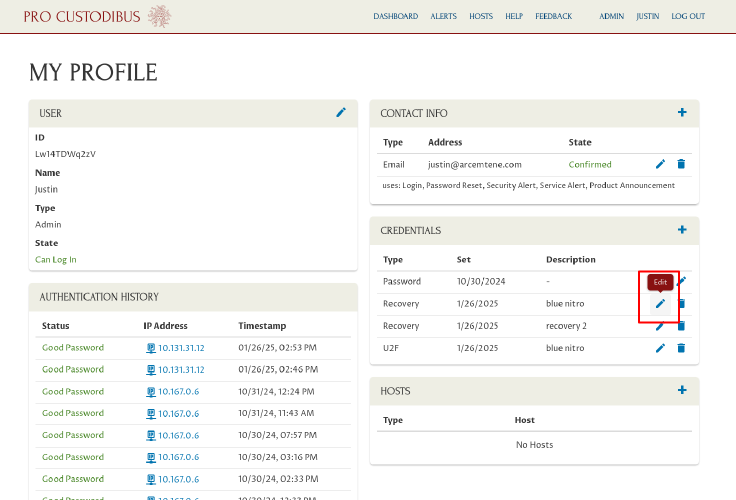
If you want to change the description of a recovery code (or secondary-verification device), you can do so by clicking the Edit icon corresponding to the code (or device) in the Credentials panel:
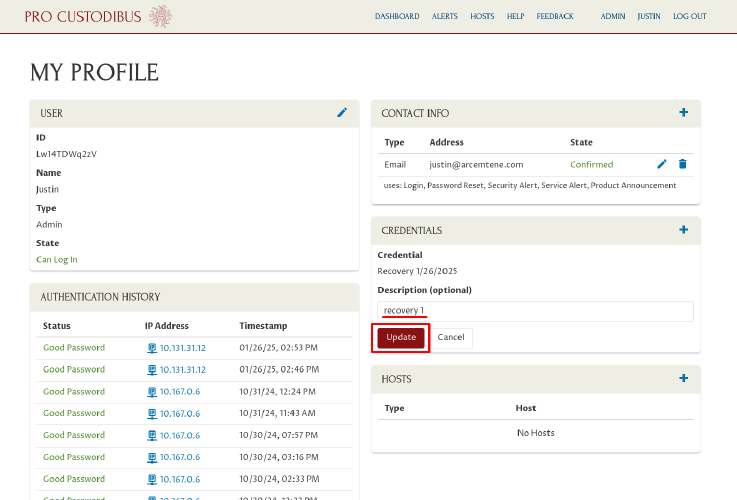
Enter a new description in the Description field, and then click the Update button:
Send a Bypass Code
If you are a Pro Custodibus admin user, and a colleague has locked himself out of Pro Custodibus, without access to any of his secondary-verification devices or recovery codes, you can send the colleague a one-time secondary-verification bypass code.
To do so, navigate to the colleague’s profile page, and click the Send Bypass icon corresponding to one of the colleague’s secondary-verification devices:
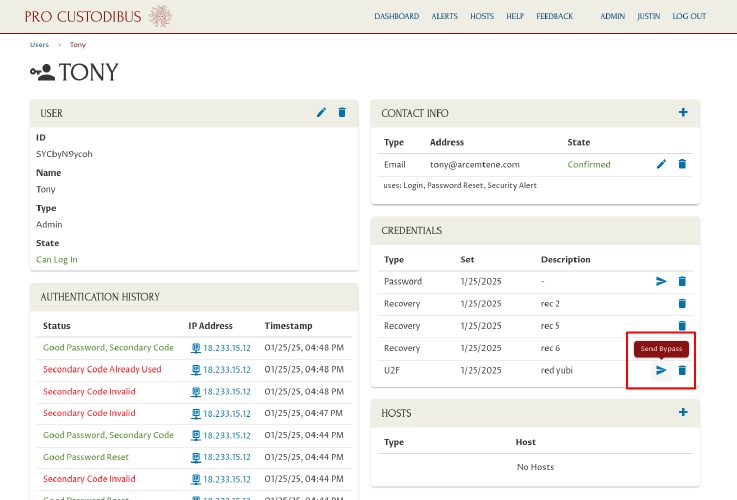
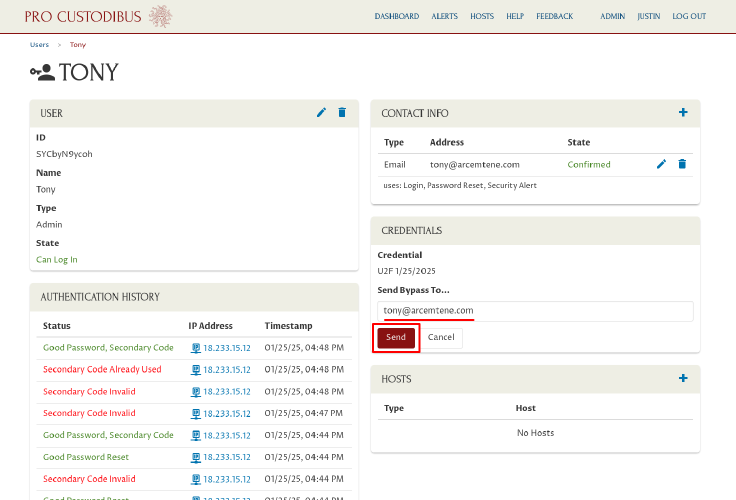
Select one of the colleague’s email addresses (or enter a different email address, if necessary) in the Send Bypasss To… field; then click the Send button:
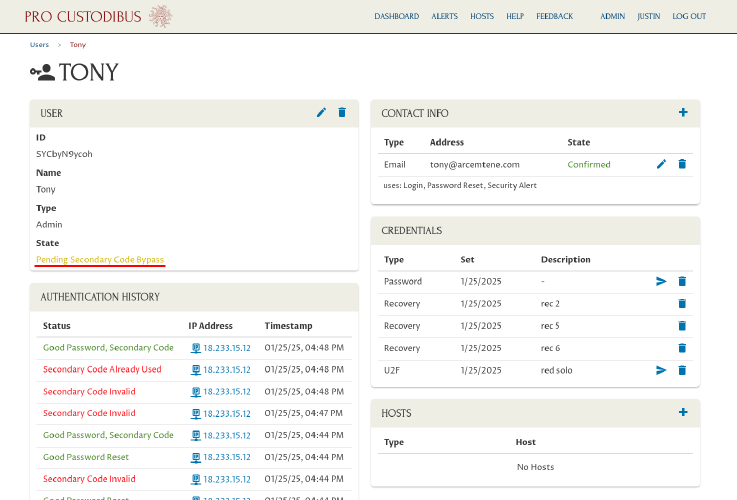
The bypass code will be good for one use only over the course of the next three days. Until the code is used (or expires), its pending state will be noted in the State field for the colleague’s user account:
The colleague can enter the code he receives by email into the Verification Code field of the Secondary Verification Required dialog on the Log In page, after he enters his existing login ID and password: